File Upload Mime Headers Garbled
File Upload Mime Headers Garbled' title='File Upload Mime Headers Garbled' />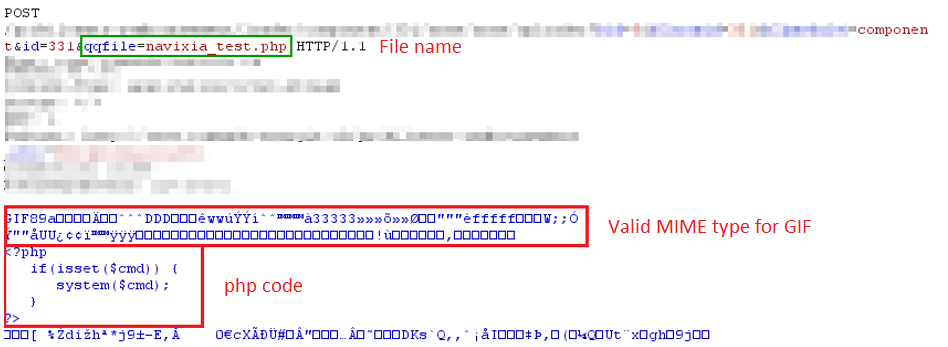

 Release Notes for the Cisco ASA 5. Series, 8. 2xTable of Contents. So, for example, a file named page. UTF8 charset attached, the difference being that if there is an. View and Download Fuji Xerox DocuCentreII 2055 user manual online. DocuCentreII 2055 All in One Printer pdf manual download. Changes sections are chronologically ordered from top most recent to bottom least recent Version 3. Summary New and Noteworthy Incompatible changes. File Upload Mime Headers Garbled' title='File Upload Mime Headers Garbled' />Release Notes for the Cisco ASA 5. Series, Version 8. Important Notes. Limitations and Restrictions. Upgrading the Software. Downloading Software from Cisco. Upgrading Between Major Releases. Upgrading the Phone Proxy and MTA Instance. Activation Key Compatibility When Upgrading. System Requirements. Memory Requirements. Standard DRAM and Internal Flash Memory. Memory Upgrade Kits. Viewing Flash Memory. DRAM, Flash Memory, and Failover. ASDM, Module, and VPN Compatibility. New Features. New Features in Version 8. New Features in Version 8. New Features in Version 8. New Features in Version 8. Mountain Rescue Training Manual there. New Features in Version 8. New Features in Version 8. Cartier Serial Number Ring. New Features in Version 8. New Features in Version 8. New Features in Version 8. Open Caveats. Resolved Caveats. Resolved Caveats in Version 8. Resolved Caveats in Version 8. Resolved Caveats in Version 8. Resolved Caveats in Version 8. Related Documentation. Obtaining Documentation and Submitting a Service Request. Release Notes for the Cisco ASA 5. Series, Version 8. Released May 8, 2. Updated July 1. 2, 2. This document contains release information for Cisco ASA 5. Versions 8. 21 through 8. This document includes the following sections Important Notes. Cisco ASA Clientless SSL VPN Portal Customization Integrity VulnerabilityMultiple vulnerabilities have been fixed for clientless SSL VPN in ASA software, so you should upgrade your software to a fixed version. See http tools. Cisco. Security. Advisorycisco sa 2. ASA versions. Also, if you ever ran an earlier ASA version that had a vulnerable configuration, then regardless of the version you are currently running, you should verify that the portal customization was not compromised. If an attacker compromised a customization object in the past, then the compromised object stays persistent after you upgrade the ASA to a fixed version. Upgrading the ASA prevents this vulnerability from being exploited further, but it will not modify any customization objects that were already compromised and are still present on the system. The Advanced Inspection and Prevention Security Services Card AIP SSC can take up to 2. This initialization process must complete before configuration changes can be made to the sensor. Attempts to modify and save configuration changes before the initialization completes will result in an error. See the Upgrading the Software section for downgrade issues after you upgrade the Phone Proxy and MTA instance, or if you upgrade the activation key with new 8. For detailed information and FAQs about feature licenses, including shared licenses and temporary licenses, see Managing Feature Licenses for Cisco ASA 5. Version 8. 2 at http www. USdocssecurityasaasa. When using Clientless SSL VPN Post SSO parameters for the Citrix Web interface bookmark, Single Sign On SSO works, but the Citrix portal is missing the Reconnect and Disconnect buttons. Only the Log Off button appears. When not using SSO over Clientless, all three buttons show up correctly. Workaround Use the Cisco HTTP POST plug in to provide SSO and correct Citrix portal behavior. On the ASA 5. 51. Version 8. 2 uses more base memory than previous releases. This might cause problems for some ASA 5. If your current show memory command output displays less than 2. ASA 5. 51. 0 from 2. MB to 1 GB before proceeding with the Version 8. See the Memory Requirements section. On the ASA 5. 58. Version 8. 2 shows increased CPU usage under stressed conditions than Version 8. Connection ProfileTunnel Group terminology in CLI vs. ASDMThe ASA tunnel groups define the initial connection parameters and attributes such as AAA, client address assignment, and connection aliasgroup url for a remote access VPN session. In the CLI, they are referred to as tunnel groups, whereas in ASDM they are referred to as Connection Profiles. A VPN policy is an aggregation of Connection Profile, Group Policy, and Dynamic Access Policy authorization attributes. Cosmetic startup message issue on the ASA 5. XCisco manufacturing recently discovered a process error that resulted in loading a test build of BIOS firmware on many early shipments of the ASA 5. X. On the affected units, more text than usual displays on the console during startup before reaching the rommon prompt. Included in the extra output is the following message banner CISCO SYSTEMS Spyker Build, TEST build not for Customer Release Embedded BIOS Version 2. While you may see this additional text, there is no functional impact to the ASA operation you can ignore the additional text. The test build provides additional information that can be used by engineers to pinpoint hardware problems during the manufacturing process. Unfortunately, there is no field upgradeable resolution to eliminate this message that does not require replacing the hardware. Hardware with a serial number that falls within the following ranges could be impacted by this cosmetic issue. Note that not all serial numbers within these ranges are impacted. JMX1. JMX1. 52. 0xxxx JAF1. JAF1. 51. 6xxxx for ASA SSP 2. K8 onlyHardware with the following Product IDs for the above serial numbers could be impacted by this cosmetic issue ASA5. S2. 0 K8 ASA5. S2. K9 ASA5. 58. S2. 0P2. K8 ASA5. S2. 0P2. K9 ASA5. S2. 0P2. XK9 ASA5. S2. 0X K9 ASA SSP 2. K8Only 4 GB of memory is available in ASA 8. ASA 5. 58. 0 and 5. X platforms. All available memory in multi core platforms ASA 5. X in ASA 8. 25 are also available in ASA 8. To take advantage of the enhanced capability, you should upgrade your devices to the ASA 8. Limitations and Restrictions. The SSL SHA 2 digital signature capability for authentication of Any. Connect SSL VPN sessions Versions 2. ASA Version 8. 2. The feature was introduced in ASA interim Version 8. Stateful Failover with Phone ProxyWhen using Stateful Failover with phone proxy, information is not passed to the standby unit when the active unit goes down, the call fails, media stops flowing, and the call must be re established. No. NET over Clientless sessionsClientless sessions do not support. NET framework applications CSCsv. The ASA does not support phone proxy and CIPC for remote access. The AIP SSC 5 does not support virtualization, unretiring default retired signatures, creating custom signatures, adding signatures, cloning signatures, or anomaly detection. The ASA cannot fully support domain based DFS. To support this, the ASA would need to join the Active Directory and query the Active Directory server for DFS referral. Instead the ASA sends the DFS referral to the DNS servers configured for the users. Since the AD server is the DNS server in most cases, the majority of customer configurations are covered. ASA 5. ASA 5. 52. ASA 5. ASA 5. 55. We strongly recommend that you enable hardware processing using the crypto engine large mod accel command instead of software for large modulus operations such as 2. DH5 keys. If you continue to use software processing for large keys, you could experience significant performance degradation due to slow session establishment for IPsec and SSL VPN connections. We recommend that you initially enable hardware processing during a low use or maintenance period to minimize a temporary packet loss that can occur during the transition of processing from software to hardware. Note For the ASA 5. BI RA WBI Web Intelligence Contributor Corner Read onlySkip to end of metadata. Go to start of metadata. BI RA WBI 1. 18. How do you cache scheduled documents to the repository for f 0. BI RA WBI 1. 18. You are unable to access the Administrator Panel after you u 1. BI RA WBI 1. 18. How do you modify the number of categories or the number of 1. BI RA WBI 1. 18. Error wstart or wstop script fail to run. BI RA WBI 1. 18. The option Center Value Across Break full client Business 0. BI RA WBI 1. 18. You upgrade from Business. Objects version 5. BI RA WBI 1. 18. Error Problem occurred during attempt to send the document 1. BI RA WBI 1. 18. Error Business. Objects server process raised an automation 3. BI RA WBI 1. 18. Error No available universe WI0. BI RA WBI 1. 18. The prompt screen takes a long time to appear when you refre 2. BI RA WBI 1. 18. What is stored in the Web. Intelligence Storage directories an 2. BI RA WBI 1. 18. What is the purpose of the parameter Kill Bus. Obj processes 1. 3. BI RA WBI 1. 18. Doctor Watson on NPH pa. Web. I is running. BI RA WBI 1. 18. How do you automatically modify the PRM file for Business. Obj 2. 6. 0. 4. 2. BI RA WBI 1. 18. Error java. IOException when you want to see the membe 0. BI RA WBI 1. 18. You must manually open documents with Business. Objects in 3 t 0. BI RA WBI 1. 18. How do you purge data or have no data returned in a Web. Intel 1. 6. 0. 5. BI RA WBI 1. 18. You cannot download Business. Objects in 3 tier mode ZABO an 2. BI RA WBI 1. 18. GPF errors are returned when you log into Web. Intelligence wi 1. BI RA WBI 1. 18. Error Cant connect to the cluster manager and all. BI RA WBI 1. 18. Error top. BI RA WBI 1. 18. The Business. Objects Services Administrator installed on a Pe 1. BI RA WBI 1. 18. How do you stop all of the Web. Intelligence Services, includi 1. BI RA WBI 1. 18. You are not receiving the most recent list of documents in W 2. BI RA WBI 1. 18. After you download the Active. X applet a second time, in a di 1. BI RA WBI 1. 18. How do you change the source for an OLAP Web. Intelligence rep 2. BI RA WBI 1. 18. What is the correct way to upgrade to a newer maintenance or 3. BI RA WBI 1. 18. Tracing the oad and the osagent with the v parameter flag 1. BI RA WBI 1. 18. In Web. Intelligence, the message not allowed is displayed 2. BI RA WBI 1. 18. Error Page cannot display when you try to connect to Web 2. BI RA WBI 1. 18. How do you print all of the report tabs in a Web. Intelligence 0. 9. BI RA WBI 1. 18. How do you trace WIDispatch, WIGenerator, wiqt, and WISessio 0. BI RA WBI 1. 18. What are the files wininet. BI RA WBI 1. 18. Error Unable to connect. Possible causes Authentication, 3. BI RA WBI 1. 18. The Web. Intelligence Administrator hangs, or nothing happens 1. BI RA WBI 1. 18. How do you drill on reports with a calculation on the measur 2. BI RA WBI 1. 18. How do you remove only the option Create and Edit Documents 0. BI RA WBI 1. 18. Error HTTP Error 4. Unauthorized Logon Failed due 0. BI RA WBI 1. 18. It is not possible to set the Web. Intelligence Admin user to 2. BI RA WBI 1. 18. How do you install Web. Intelligence on one machine, and a Web 0. BI RA WBI 1. 18. An empty page containing a red cross is displayed inside the 1. BI RA WBI 1. 18. How do you optimize the performance of Web. Intelligence on Wi 1. BI RA WBI 1. 18. Error Activation Daemon Timed out The following registra 1. BI RA WBI 1. 18. Web. Intelligence Enhanced Document format does not display ce 2. BI RA WBI 1. 18. How do you change the Web. Intelligence Administrative user wi 0. BI RA WBI 1. 18. Error Your license is not valid when starting Web. Intelli 1. 3. 0. 5. BI RA WBI 1. 18. Error HTTP 4. Page not found when you are using Activ 1. BI RA WBI 1. 18. Error Error type OX8. Permission to use objects de 2. BI RA WBI 1. 18. The WIGenerator consumes a large amount of CPU when you sele 0. BI RA WBI 1. 18. Error Invalid page fault 1. H in rptviewerax. BI RA WBI 1. 18. Error Event ID 2. Action timed out for Bus. Obj server pr 1. 0. BI RA WBI 1. 18. Personal document descriptions and keywords are lost after y 0. BI RA WBI 1. 18. How do you access the data that is held in a Java object and 1. BI RA WBI 1. 18. You cannot display pie charts containing percentage values i 0. BI RA WBI 1. 18. Why is it recommended that you have the WISYS environment va 0. BI RA WBI 1. 18. You are unable to download the Web. Intelligence Full Java App 0. BI RA WBI 1. 18. How do you use a special font in a UNIX full client Business 0. BI RA WBI 1. 18. You start Web. Intelligence or Broadcast Agent, but not all of 0. BI RA WBI 1. 18. The dates entered in the prompts are always interpreted in t 0. BI RA WBI 1. 18. Error The page cannot be found http 4. File not Found 0. BI RA WBI 1. 18. Error Cannot connect to Cluster Manager when you log int 1. BI RA WBI 1. 18. When you use the Enhanced Document Active. X Viewer, some of 0. BI RA WBI 1. 18. How do you configuring i. Planet 6. 0 on Windows NT4 or 2. BI RA WBI 1. 18. Error HTTP1. Access Denied when you try to log int 1. BI RA WBI 1. 18. Why does Web. IntelligenceBusiness. Objects in 3 tier mode ZAB 0. BI RA WBI 1. 18. Where are the Web. Intelligence settings stored on a Windows N 2. BI RA WBI 1. 18. The Web. Intelligence Administrator Tool and the Java Applet q 0. BI RA WBI 1. 18. You cannot run a macro defined on a full client Business. Obje 2. 4. 0. 5. 2. BI RA WBI 1. 18. What information is stored in the file Corp. BI RA WBI 1. 18. Error Your Web. Intelligence Session has ended, chart canno 2. BI RA WBI 1. 18. Why do the Info. View sessions sometimes end later than the se 0. BI RA WBI 1. 18. Using Tab as a list separator in Web. Intelligence when downlo 2. BI RA WBI 1. 18. The WISite. Log traces cannot be turned on in Web. Intelligence 2. 4. BI RA WBI 1. 18. Error Exception java. Class. Not. Found. Exception bo. wi. BI RA WBI 1. 18. Error This page is empty when you try to open or refresh 2. BI RA WBI 1. 18. How do you determine if there is a proxy installed between y 2. BI RA WBI 1. 18. What can you do to get more information on a core dumpBI RA WBI 1. Error Cannot connect to Cluster Manager when you try to 0. BI RA WBI 1. 18. Can you use the Web Server Basic Authentication with the Bus 1. BI RA WBI 1. 18. You receive a blank screen when you click on the OLAP Data S 1. BI RA WBI 1. 18. Error Access to the universe or editing of document is no 1. BI RA WBI 1. 18. How do you disable logging to the Webi. Server. log file ever 2. BI RA WBI 1. 18. Error You are not Authorized when you try to use NT Auth 1. BI RA WBI 1. 18. You use the Web. Intelligence Enhanced Document Viewer to view 0. BI RA WBI 1. 18. How do you create Web. Intelligence reports using personalized 3. BI RA WBI 1. 18. How do you configure the Web. Intelligence authentication meth 2. BI RA WBI 1. 18. What is the purpose of the Web. Intelligence option Download 2. BI RA WBI 1. 18. The File Monitor shows that Business. Objects components are a 1. BI RA WBI 1. 18. Why do a users Personal Documents disappear in Web. Intellige 2. 9. 0. BI RA WBI 1. 18. The Web. Intelligence SDK module is not listed in the Choose 1. BI RA WBI 1. 18. What joins are located between the Audit Facility Tables BI RA WBI 1. What happens with the BOManager processs Min Number of Loa 2. BI RA WBI 1. 18. Why do the WIStorage.
Release Notes for the Cisco ASA 5. Series, 8. 2xTable of Contents. So, for example, a file named page. UTF8 charset attached, the difference being that if there is an. View and Download Fuji Xerox DocuCentreII 2055 user manual online. DocuCentreII 2055 All in One Printer pdf manual download. Changes sections are chronologically ordered from top most recent to bottom least recent Version 3. Summary New and Noteworthy Incompatible changes. File Upload Mime Headers Garbled' title='File Upload Mime Headers Garbled' />Release Notes for the Cisco ASA 5. Series, Version 8. Important Notes. Limitations and Restrictions. Upgrading the Software. Downloading Software from Cisco. Upgrading Between Major Releases. Upgrading the Phone Proxy and MTA Instance. Activation Key Compatibility When Upgrading. System Requirements. Memory Requirements. Standard DRAM and Internal Flash Memory. Memory Upgrade Kits. Viewing Flash Memory. DRAM, Flash Memory, and Failover. ASDM, Module, and VPN Compatibility. New Features. New Features in Version 8. New Features in Version 8. New Features in Version 8. New Features in Version 8. Mountain Rescue Training Manual there. New Features in Version 8. New Features in Version 8. Cartier Serial Number Ring. New Features in Version 8. New Features in Version 8. New Features in Version 8. Open Caveats. Resolved Caveats. Resolved Caveats in Version 8. Resolved Caveats in Version 8. Resolved Caveats in Version 8. Resolved Caveats in Version 8. Related Documentation. Obtaining Documentation and Submitting a Service Request. Release Notes for the Cisco ASA 5. Series, Version 8. Released May 8, 2. Updated July 1. 2, 2. This document contains release information for Cisco ASA 5. Versions 8. 21 through 8. This document includes the following sections Important Notes. Cisco ASA Clientless SSL VPN Portal Customization Integrity VulnerabilityMultiple vulnerabilities have been fixed for clientless SSL VPN in ASA software, so you should upgrade your software to a fixed version. See http tools. Cisco. Security. Advisorycisco sa 2. ASA versions. Also, if you ever ran an earlier ASA version that had a vulnerable configuration, then regardless of the version you are currently running, you should verify that the portal customization was not compromised. If an attacker compromised a customization object in the past, then the compromised object stays persistent after you upgrade the ASA to a fixed version. Upgrading the ASA prevents this vulnerability from being exploited further, but it will not modify any customization objects that were already compromised and are still present on the system. The Advanced Inspection and Prevention Security Services Card AIP SSC can take up to 2. This initialization process must complete before configuration changes can be made to the sensor. Attempts to modify and save configuration changes before the initialization completes will result in an error. See the Upgrading the Software section for downgrade issues after you upgrade the Phone Proxy and MTA instance, or if you upgrade the activation key with new 8. For detailed information and FAQs about feature licenses, including shared licenses and temporary licenses, see Managing Feature Licenses for Cisco ASA 5. Version 8. 2 at http www. USdocssecurityasaasa. When using Clientless SSL VPN Post SSO parameters for the Citrix Web interface bookmark, Single Sign On SSO works, but the Citrix portal is missing the Reconnect and Disconnect buttons. Only the Log Off button appears. When not using SSO over Clientless, all three buttons show up correctly. Workaround Use the Cisco HTTP POST plug in to provide SSO and correct Citrix portal behavior. On the ASA 5. 51. Version 8. 2 uses more base memory than previous releases. This might cause problems for some ASA 5. If your current show memory command output displays less than 2. ASA 5. 51. 0 from 2. MB to 1 GB before proceeding with the Version 8. See the Memory Requirements section. On the ASA 5. 58. Version 8. 2 shows increased CPU usage under stressed conditions than Version 8. Connection ProfileTunnel Group terminology in CLI vs. ASDMThe ASA tunnel groups define the initial connection parameters and attributes such as AAA, client address assignment, and connection aliasgroup url for a remote access VPN session. In the CLI, they are referred to as tunnel groups, whereas in ASDM they are referred to as Connection Profiles. A VPN policy is an aggregation of Connection Profile, Group Policy, and Dynamic Access Policy authorization attributes. Cosmetic startup message issue on the ASA 5. XCisco manufacturing recently discovered a process error that resulted in loading a test build of BIOS firmware on many early shipments of the ASA 5. X. On the affected units, more text than usual displays on the console during startup before reaching the rommon prompt. Included in the extra output is the following message banner CISCO SYSTEMS Spyker Build, TEST build not for Customer Release Embedded BIOS Version 2. While you may see this additional text, there is no functional impact to the ASA operation you can ignore the additional text. The test build provides additional information that can be used by engineers to pinpoint hardware problems during the manufacturing process. Unfortunately, there is no field upgradeable resolution to eliminate this message that does not require replacing the hardware. Hardware with a serial number that falls within the following ranges could be impacted by this cosmetic issue. Note that not all serial numbers within these ranges are impacted. JMX1. JMX1. 52. 0xxxx JAF1. JAF1. 51. 6xxxx for ASA SSP 2. K8 onlyHardware with the following Product IDs for the above serial numbers could be impacted by this cosmetic issue ASA5. S2. 0 K8 ASA5. S2. K9 ASA5. 58. S2. 0P2. K8 ASA5. S2. 0P2. K9 ASA5. S2. 0P2. XK9 ASA5. S2. 0X K9 ASA SSP 2. K8Only 4 GB of memory is available in ASA 8. ASA 5. 58. 0 and 5. X platforms. All available memory in multi core platforms ASA 5. X in ASA 8. 25 are also available in ASA 8. To take advantage of the enhanced capability, you should upgrade your devices to the ASA 8. Limitations and Restrictions. The SSL SHA 2 digital signature capability for authentication of Any. Connect SSL VPN sessions Versions 2. ASA Version 8. 2. The feature was introduced in ASA interim Version 8. Stateful Failover with Phone ProxyWhen using Stateful Failover with phone proxy, information is not passed to the standby unit when the active unit goes down, the call fails, media stops flowing, and the call must be re established. No. NET over Clientless sessionsClientless sessions do not support. NET framework applications CSCsv. The ASA does not support phone proxy and CIPC for remote access. The AIP SSC 5 does not support virtualization, unretiring default retired signatures, creating custom signatures, adding signatures, cloning signatures, or anomaly detection. The ASA cannot fully support domain based DFS. To support this, the ASA would need to join the Active Directory and query the Active Directory server for DFS referral. Instead the ASA sends the DFS referral to the DNS servers configured for the users. Since the AD server is the DNS server in most cases, the majority of customer configurations are covered. ASA 5. ASA 5. 52. ASA 5. ASA 5. 55. We strongly recommend that you enable hardware processing using the crypto engine large mod accel command instead of software for large modulus operations such as 2. DH5 keys. If you continue to use software processing for large keys, you could experience significant performance degradation due to slow session establishment for IPsec and SSL VPN connections. We recommend that you initially enable hardware processing during a low use or maintenance period to minimize a temporary packet loss that can occur during the transition of processing from software to hardware. Note For the ASA 5. BI RA WBI Web Intelligence Contributor Corner Read onlySkip to end of metadata. Go to start of metadata. BI RA WBI 1. 18. How do you cache scheduled documents to the repository for f 0. BI RA WBI 1. 18. You are unable to access the Administrator Panel after you u 1. BI RA WBI 1. 18. How do you modify the number of categories or the number of 1. BI RA WBI 1. 18. Error wstart or wstop script fail to run. BI RA WBI 1. 18. The option Center Value Across Break full client Business 0. BI RA WBI 1. 18. You upgrade from Business. Objects version 5. BI RA WBI 1. 18. Error Problem occurred during attempt to send the document 1. BI RA WBI 1. 18. Error Business. Objects server process raised an automation 3. BI RA WBI 1. 18. Error No available universe WI0. BI RA WBI 1. 18. The prompt screen takes a long time to appear when you refre 2. BI RA WBI 1. 18. What is stored in the Web. Intelligence Storage directories an 2. BI RA WBI 1. 18. What is the purpose of the parameter Kill Bus. Obj processes 1. 3. BI RA WBI 1. 18. Doctor Watson on NPH pa. Web. I is running. BI RA WBI 1. 18. How do you automatically modify the PRM file for Business. Obj 2. 6. 0. 4. 2. BI RA WBI 1. 18. Error java. IOException when you want to see the membe 0. BI RA WBI 1. 18. You must manually open documents with Business. Objects in 3 t 0. BI RA WBI 1. 18. How do you purge data or have no data returned in a Web. Intel 1. 6. 0. 5. BI RA WBI 1. 18. You cannot download Business. Objects in 3 tier mode ZABO an 2. BI RA WBI 1. 18. GPF errors are returned when you log into Web. Intelligence wi 1. BI RA WBI 1. 18. Error Cant connect to the cluster manager and all. BI RA WBI 1. 18. Error top. BI RA WBI 1. 18. The Business. Objects Services Administrator installed on a Pe 1. BI RA WBI 1. 18. How do you stop all of the Web. Intelligence Services, includi 1. BI RA WBI 1. 18. You are not receiving the most recent list of documents in W 2. BI RA WBI 1. 18. After you download the Active. X applet a second time, in a di 1. BI RA WBI 1. 18. How do you change the source for an OLAP Web. Intelligence rep 2. BI RA WBI 1. 18. What is the correct way to upgrade to a newer maintenance or 3. BI RA WBI 1. 18. Tracing the oad and the osagent with the v parameter flag 1. BI RA WBI 1. 18. In Web. Intelligence, the message not allowed is displayed 2. BI RA WBI 1. 18. Error Page cannot display when you try to connect to Web 2. BI RA WBI 1. 18. How do you print all of the report tabs in a Web. Intelligence 0. 9. BI RA WBI 1. 18. How do you trace WIDispatch, WIGenerator, wiqt, and WISessio 0. BI RA WBI 1. 18. What are the files wininet. BI RA WBI 1. 18. Error Unable to connect. Possible causes Authentication, 3. BI RA WBI 1. 18. The Web. Intelligence Administrator hangs, or nothing happens 1. BI RA WBI 1. 18. How do you drill on reports with a calculation on the measur 2. BI RA WBI 1. 18. How do you remove only the option Create and Edit Documents 0. BI RA WBI 1. 18. Error HTTP Error 4. Unauthorized Logon Failed due 0. BI RA WBI 1. 18. It is not possible to set the Web. Intelligence Admin user to 2. BI RA WBI 1. 18. How do you install Web. Intelligence on one machine, and a Web 0. BI RA WBI 1. 18. An empty page containing a red cross is displayed inside the 1. BI RA WBI 1. 18. How do you optimize the performance of Web. Intelligence on Wi 1. BI RA WBI 1. 18. Error Activation Daemon Timed out The following registra 1. BI RA WBI 1. 18. Web. Intelligence Enhanced Document format does not display ce 2. BI RA WBI 1. 18. How do you change the Web. Intelligence Administrative user wi 0. BI RA WBI 1. 18. Error Your license is not valid when starting Web. Intelli 1. 3. 0. 5. BI RA WBI 1. 18. Error HTTP 4. Page not found when you are using Activ 1. BI RA WBI 1. 18. Error Error type OX8. Permission to use objects de 2. BI RA WBI 1. 18. The WIGenerator consumes a large amount of CPU when you sele 0. BI RA WBI 1. 18. Error Invalid page fault 1. H in rptviewerax. BI RA WBI 1. 18. Error Event ID 2. Action timed out for Bus. Obj server pr 1. 0. BI RA WBI 1. 18. Personal document descriptions and keywords are lost after y 0. BI RA WBI 1. 18. How do you access the data that is held in a Java object and 1. BI RA WBI 1. 18. You cannot display pie charts containing percentage values i 0. BI RA WBI 1. 18. Why is it recommended that you have the WISYS environment va 0. BI RA WBI 1. 18. You are unable to download the Web. Intelligence Full Java App 0. BI RA WBI 1. 18. How do you use a special font in a UNIX full client Business 0. BI RA WBI 1. 18. You start Web. Intelligence or Broadcast Agent, but not all of 0. BI RA WBI 1. 18. The dates entered in the prompts are always interpreted in t 0. BI RA WBI 1. 18. Error The page cannot be found http 4. File not Found 0. BI RA WBI 1. 18. Error Cannot connect to Cluster Manager when you log int 1. BI RA WBI 1. 18. When you use the Enhanced Document Active. X Viewer, some of 0. BI RA WBI 1. 18. How do you configuring i. Planet 6. 0 on Windows NT4 or 2. BI RA WBI 1. 18. Error HTTP1. Access Denied when you try to log int 1. BI RA WBI 1. 18. Why does Web. IntelligenceBusiness. Objects in 3 tier mode ZAB 0. BI RA WBI 1. 18. Where are the Web. Intelligence settings stored on a Windows N 2. BI RA WBI 1. 18. The Web. Intelligence Administrator Tool and the Java Applet q 0. BI RA WBI 1. 18. You cannot run a macro defined on a full client Business. Obje 2. 4. 0. 5. 2. BI RA WBI 1. 18. What information is stored in the file Corp. BI RA WBI 1. 18. Error Your Web. Intelligence Session has ended, chart canno 2. BI RA WBI 1. 18. Why do the Info. View sessions sometimes end later than the se 0. BI RA WBI 1. 18. Using Tab as a list separator in Web. Intelligence when downlo 2. BI RA WBI 1. 18. The WISite. Log traces cannot be turned on in Web. Intelligence 2. 4. BI RA WBI 1. 18. Error Exception java. Class. Not. Found. Exception bo. wi. BI RA WBI 1. 18. Error This page is empty when you try to open or refresh 2. BI RA WBI 1. 18. How do you determine if there is a proxy installed between y 2. BI RA WBI 1. 18. What can you do to get more information on a core dumpBI RA WBI 1. Error Cannot connect to Cluster Manager when you try to 0. BI RA WBI 1. 18. Can you use the Web Server Basic Authentication with the Bus 1. BI RA WBI 1. 18. You receive a blank screen when you click on the OLAP Data S 1. BI RA WBI 1. 18. Error Access to the universe or editing of document is no 1. BI RA WBI 1. 18. How do you disable logging to the Webi. Server. log file ever 2. BI RA WBI 1. 18. Error You are not Authorized when you try to use NT Auth 1. BI RA WBI 1. 18. You use the Web. Intelligence Enhanced Document Viewer to view 0. BI RA WBI 1. 18. How do you create Web. Intelligence reports using personalized 3. BI RA WBI 1. 18. How do you configure the Web. Intelligence authentication meth 2. BI RA WBI 1. 18. What is the purpose of the Web. Intelligence option Download 2. BI RA WBI 1. 18. The File Monitor shows that Business. Objects components are a 1. BI RA WBI 1. 18. Why do a users Personal Documents disappear in Web. Intellige 2. 9. 0. BI RA WBI 1. 18. The Web. Intelligence SDK module is not listed in the Choose 1. BI RA WBI 1. 18. What joins are located between the Audit Facility Tables BI RA WBI 1. What happens with the BOManager processs Min Number of Loa 2. BI RA WBI 1. 18. Why do the WIStorage.